This is the first of a series of posts about interesting things we have found in the DNS traffic of the .uk zone using our Turing DNS analysis tool, which has enabled us to identify cyber security threats, server misconfigurations and software bugs. This first story is about a bug we discovered in the popular BIND DNS software.
BIND is the most widely used software for running DNS servers. Using our Turing DNS traffic analysis tool we identified a bug in the software that posed a significant risk to the underlying infrastructure of the internet with the potential to render large parts of the internet inaccessible.
BIND can be run in different modes and so has lots of functionality built in; at Nominet we use perhaps the simplest as we run authoritative servers. However; we have a lot of code deployed that we do not actually use, e.g. the code required to run as a recursive server.
Furthermore, we understand exactly what sorts of DNS requests we should be getting and, more importantly, what sorts of responses we should be sending. As an example, part of the dynamic updates protocol allows for prerequisites to be specified “if this domain exists do that” We don’t use this mechanism and so its related response of “NXRRSET” should never be sent. (Any attempt to trigger this should be caught earlier as the request would not be properly authorised).
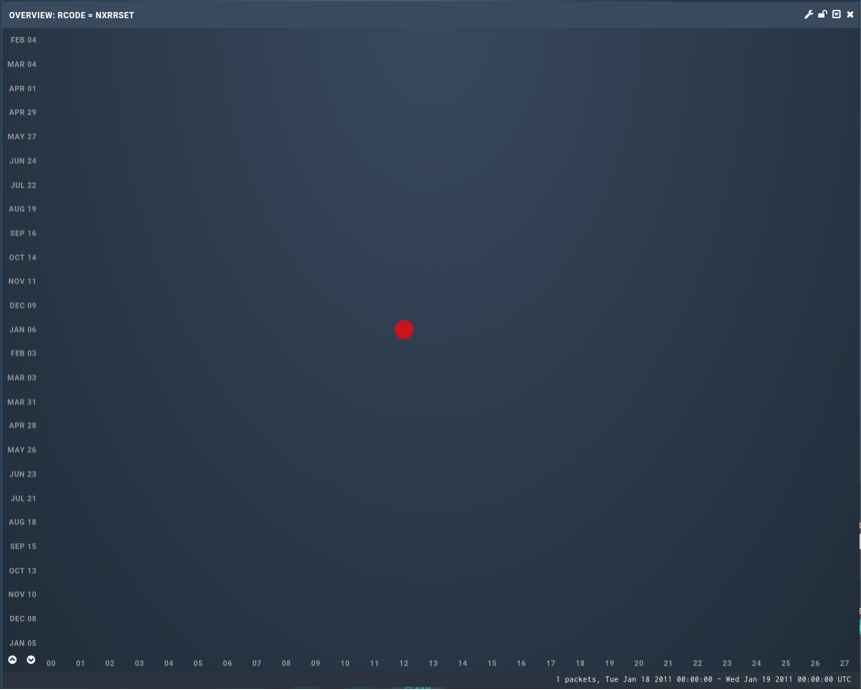
However, in January 2011, we saw one of our nameservers sending exactly this response. Just one instance of it, so it shows up very clearly when we used Turing to filter for just that particular response code, as shown below:
This view spans two years and shows a single instance of us responding NXRRSET.
We decided to further investigate this DNS message to work out how this happened. While the original message itself was harmless, by tweaking the message slightly we discovered that it could force a DNS server running (even recent versions of) the BIND software to reboot, essentially making them unavailable for a few minutes at a time. If the server was sent this message on a regular basis, it could take it offline indefinitely. We estimated that you would only need to send a few thousand of these messages a minute to the main DNS servers in any Western country to render the majority of websites there inaccessible. This was clearly a major risk to the underlying infrastructure of the internet, so once we had confirmed the issue we quickly informed the company that owns the BIND software, Internet Systems Consortium (ISC), about the bug. ISC was then able to fix the bug and release an update (CVE-2011-2464) that removed the threat.